Introduction
Jump to...
- What is IT documentation?
- Why IT documentation is important
- Types of IT documentation
- IT documentation templates & examples
- IT documentation best practices
- Start your IT documentation today
IT documentation is an invaluable resource for managed service providers and other IT professionals. It lets them both collect and keep track of crucial business data.
There’s a lot of wasted time and energy because of the lack of documentation. Your competitive edge will suffer, and your client relationships can be at risk.
Here’s the good news: using IT documentation templates, you can prevent all of this.

IT administrators are always on the lookout for new ways to include this program in their daily routines because it's so adaptable.
A contemporary, safe IT infrastructure relies on a solid foundation of organizational knowledge, and IT documentation software helps users lay down those bricks.
Create AI-powered documentation for free ➜
TL;DR: IT documentation templates & examples
- IT documentation is crucial for managed service providers and IT professionals to collect and track important business data.
- It includes various types of documentation such as device, environmental, process, credentials, incident response, infrastructure, project, technical, user, and network documentation.
- IT documentation helps maintain organizational knowledge, save time and effort, facilitate new hire onboarding, reduce errors, promote standardization, and ensure quality control.
- Using IT documentation templates and following best practices can improve efficiency and effectiveness.
- Scribe automates the documentation process, making it easier and faster to create comprehensive guides for IT procedures.
What is IT documentation
Organizations, especially those whose primary focus is information technology, can’t function without thorough documentation.
Basically, when it comes to information technology, documentation is everything.
This knowledge might help the IT staff:
- Carry out a procedure.
- Work more effectively.
- Learn more.
- Lay out how to fix a problem
… and more.
IT documentation can contain so much useful information, from setups and standard operating procedures to passwords and credentials. Software specifically designed for documenting IT helps to streamline the process.
Internal stakeholders (workers, management, etc.) and external stakeholders (customers, clients, partners) can use documentation as a reference to learn about and follow a process with little to no training.
For several reasons, documentation is essential in the information technology and software fields:
- For gathering software requirements.
- For recording procedures for future use.
- For building project plans and standard operating procedures.
- For developing user guides to help new staff learn the product and pick it up fast.
- As an agreement between the client and the consumer to fulfill the promised services.
- As a guide for customers to use on their own, to get them up to speed on installing, running, and troubleshooting any issues that may arise.
- To carefully consider all aspects of a project before investing time and money into it so that unnecessary adjustments may be avoided.
- For keeping track of all the technologies that went into making the product and their respective documentation.
IT documentation, at its heart, is the orderly presentation of data to improve efficiency and outputs.
Why IT documentation is important
When you consider how much information is required to manage IT infrastructures, you'll understand the value of IT documentation.
Before now, MSPs were slow to see the value of documentation. But things have changed dramatically as MSPs and IT departments see the competitive advantage of IT documentation.
Simply put, IT documentation can help businesses develop in a competitive market while cutting down on inefficiencies.
1. Maintain organizational knowledge
When a key employee leaves for greener pastures, whether through retirement or being poached by a competitor, the void they leave in your operations may be devastating.
For this reason, businesses must implement a knowledge transfer strategy so that this vital organizational information is not lost when a worker quits.
You can also record basic corporate standard operating procedures (SOPs) or instructions for functioning devices and networks. This is crucial info, given how important this data is to IT providers' duties.
2. Save time & effort
Without sufficient IT documentation, workers might do the assignment in an unexpected way. Some people may be able to get things done fast, while others lose time trying to figure things out on their own.
Well-written, technical documentation that follows best practices guarantees that every worker completes their assigned work in the allotted time. Particularly helpful for writing SOPs, this boosts efficiency and productivity by encouraging standardization and consistency.
3. Efficient new hire onboarding
New recruits benefit greatly from the documentation that captures the knowledge of current workers.
New employees can quickly learn the company's procedures, rules and inner workings by reading the provided documents upon their arrival.
Rather than having to wait for an already busy worker to give them training, they may study at their own leisure using clear, concise and well-organized how-to guides.
4. Have fewer errors
A core resource for IT workers can be a record of all relevant data about an IT environment, together with detailed descriptions of related methodologies and activities.
You can consult it as often as necessary to ensure accuracy and maximize productivity.
A network's performance is very sensitive to any and all of its constituent parts. Forgotten passwords for Active Directory (AD) accounts, for instance, can lead to lost time and security risks if they aren't documented, but the problem can be remedied quickly and easily if the passwords are stored in a single, convenient location.
5. Effective standardization
You can standardize your IT infrastructures with the aid of documentation that includes all the important information for your company.
When all of your environments adhere to the same standards, your business activities will run more smoothly.
You’ll always have the same data on hand for any given piece, and if you want to achieve uniformity with minimal effort, your software or tools should be user-friendly, intuitive and unified or integrated across all of your most significant processes.
6. Promote quality control
Alignment and responsibility come from having everything documented. You get better outcomes when technicians are responsible for the paperwork they produce. Plus, you can develop documentation techniques according to predetermined quality benchmarks. This raises the standard of many business procedures in total.
Types of IT documentation
- Device documentation
- Environmental documentation
- Process documentation
- Credentials documentation
- Incident response documentation
- Infrastructure documentation
- Project documentation
- Technical documentation
- User documentation
- Network documentation
IT professionals would wish to record many different kinds of information for the sake of their company's performance.
Device, environment, process, credential and incident response plan documentation are all examples of what might fall under this category.
1. Device documentation
Recording the specifics of every particular device gives technicians the ability to have a rapid overview of the device's components at any given time. These particulars normally consist of the device's External IP address, operating system, and any software installed on it.
2. Environmental documentation
It might be tough to keep track of how many nodes on a network are interconnected when you're responsible for monitoring multiple IT environments.
References like network diagrams that detail the interdependencies and dependencies of various devices are sometimes in environmental documentation.
3. Process documentation
Thorough process documentation is essential for reliably following standard operating procedures.
In most cases, it specifies the appropriate contacts, procedures and approvals for achieving a certain objective or desired outcome.
This record-keeping is also useful when outlining the steps necessary to secure licenses.
4. Credentials documentation
Information technology (IT) documentation can also hold confidential data.
It’s crucial to store credentials like usernames, passwords and MFA information in a secure yet easily accessible area.
IT documentation provides firms with a practical resource that serves dual purposes.
5. Incident response documentation
If you work in IT, you can expect to face cyberattacks.
You can note how a breach happened, what was compromised, and what actions to take in response in incident response documentation.
IT professionals will feel more at ease when it comes to the inevitable cyberattacks if they have an incident response strategy in place.
6. Infrastructure documentation
This gives you insight into the technical foundation of the company. Everything is documented, from hardware gadgets to software applications. Technicians can't fix a problem until they understand the infrastructure and how it all works together.
7. Project documentation
Here you can detail out the initiatives being worked on by an organization.
Everything that has to be done for the project and the tools needed lives here. The additional project documents that will be generated throughout the course of this are likewise a major emphasis.
8. Technical documentation
You get detailed descriptions of a product's functionality, features and overall design in these documents.
Technical documentation includes anything that contains technical details, like specs, API documentation, software code details, etc.
9. User documentation
End-user documentation is the materials that consumers are supposed to read to learn about a service or product. Since it's meant to be used by regular people, you want to strip it down to the bare essentials.
10. Network documentation
Here, you'll keep tabs on your company's numerous computer networks and all the software, hardware, version numbers, security tools, connections, topology, etc., that make them tick.
IT documentation templates & examples
IT documentation templates save time and effort by providing a starting point for your work.
Using a template helps speed up the documentation process by establishing a framework for your content with standardized sections in which you can add your own information.
Here are a few IT documentation templates you can get started with today!
1. IT documentation template

Document important information about your IT systems, processes, workflows, and infrastructure. Create comprehensive and easy-to-use internal documentation with this IT Documentation Template:
- Develop a system administrator guide.
- Create IT policies and procedures documents.
- Prepare a disaster recovery plan.
- Document a software development process.
- Create a network diagram.
🎓 Related resource: 5 Software Documentation Challenges For DevOps Teams & How To Overcome Them
2. IT Standard Operating Procedures (SOPs) template

Use an IT SOP Template to outline step-by-step instructions for performing specific tasks or processes, including:
- Installing and configuring software or hardware.
- Conducting routine maintenance tasks, such as system backups or virus scans.
- Troubleshooting and resolving common IT issues.
- Managing user accounts and access permissions.
- Responding to security incidents or data breaches.
- Creating and maintaining IT policies and procedures.
- Training new IT staff.
3. Software user manual template

Use a Software User Manual Template to create accurate documentation on how to use any software application effectively and efficiently. This guide helps users understand the software's features, navigate the user interface, troubleshoot problems, and answer frequently asked questions.
Software documentation Chrome extensions like Scribe capture your screen as you navigate the software, generating step-by-step guides. Check out our blog for more details on how to use Scribe for software documentation.
4. App licensing, passwords, login credentials & details of internal infrastructure template

Use this template to outline your organization's App Licensing, Passwords, Login Credentials & Details of Internal Infrastructure.
- Keep track of app licensing.
- Enforce secure passwords.
- Secure login credentials.
- Outline network architecture, server locations and system configurations.
5. Troubleshooting guide template

Troubleshooting guides help your team quickly identify and resolve common issues, reducing the amount of time spent on troubleshooting. Use this Troubleshooting Guide Template to:
- Standardize your approach.
- Reduce time spent troubleshooting issues.
- Identify possible causes.
- Provide step-by-step instructions to solve issues.
- Speed up diagnosis.
Due to their reliability and productivity, step-by-step guide templates make it easier to keep records. Now, technicians won't have to waste time and energy guessing which details should be documented. Here are a few examples of step-by-step documentation.
1. Best practices for Google Sheets
If you only need to keep track of a few pieces of information, then using Google Sheets is an excellent alternative to hosting a database or hiring a database administrator.
However, a few problems can come from relying too much on Google Sheets.
It's easy for things to go wrong when dealing with large amounts of data, including disorganization, missing data points or accidental edits. This can waste your data collection efforts and time.
If you want to avoid problems, just follow the advice given in this Scribe tutorial.

3. How to set up ZoomInfo VoIP
VoIP is employed by many salespeople who wish to conduct phone calls through an internet connection. After establishing the connection, you can call individuals directly using ZoomInfo Engage.
Here's an example of how to set up ZoomInfo VoIP by following the instructions in this Scribe.

4. How to connect ZoomInfo Engage with your Salesforce account
Sales and marketing professionals need a system to track the customer's journey and get vital information. Here's where the benefits of ZoomInfo's Salesforce Integration come into play.
This Scribe guide provides a step-by-step guide for connecting ZoomInfo Engage and Salesforce accounts.

5. How to mass update Salesforce with dataloader.io
Data Loader can help as a client application when transferring large amounts of information across systems.
As an alternative to removing and reimporting large amounts of data, your team might use reporting and dataloader.io to update your Account data in bulk efficiently. Here's an easy-to-follow Scribe that walks your team through how to do it.

IT documentation best practices
Best practices should be followed while creating and updating IT documentation. In short? Documentation can save you time, money and energy if used correctly.
To improve the efficiency of your IT documentation, consider the following:
1. Maximize the use of automation tools wherever possible
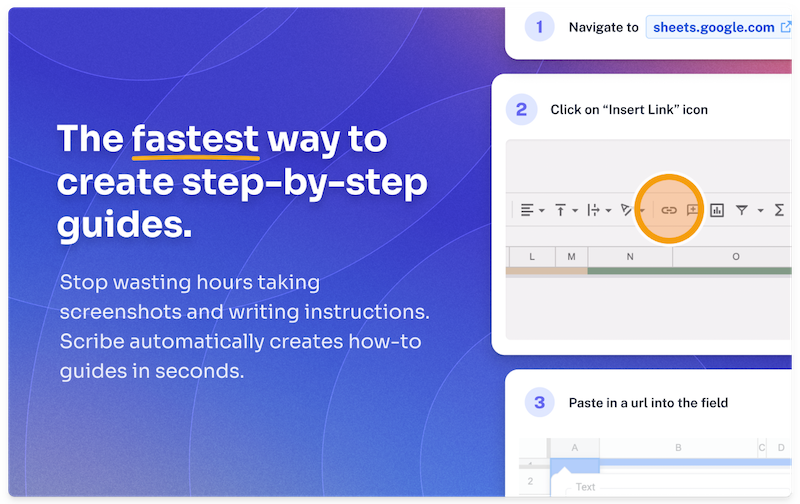
It should be simpler and faster to document your work. Surely the use of automated processes is the best method to achieve this goal. You may save a lot of time and guarantee higher accuracy by automating all the repetitive procedures involved in documenting. IT documentation Chrome extensions like Scribe automate documentation while you work.
2. Standardize formatting
You should use the same documentation format consistently. You need to implement regulations to guarantee uniformity of style across the board. This can reduce the likelihood of human mistakes and make it simpler to find relevant data in massive databases.
3. Be clear and concise
IT documentation should always prioritize clarity, completeness and precision.
If you don’t pay attention to particulars, you’ll run into complications down the line.
Careful records can help you prevent this. Your documentation doesn't have to be too wordy or complicated. The key is conciseness. Don't forget any information you think is essential.
4. Don't get too technical
Knowing your readership is important when documenting your product. Given that employees from several divisions will use this material, avoid using very technical language. In fact, don't be afraid to use everyday language.
5. Integrate images and flowcharts
An image conveys more than words alone. Include media such like videos, photos, instructions, schematics, etc.
If your documentation is wall-to-wall text, your readers may get bored or give up on them before they've even started. Use tables, graphs, flowcharts and pictures liberally to avoid this.
6. Embrace a culture of documentation
The documentation process requires more than a select few team members. It's imperative that everyone in the company strictly adhere to it. Create a culture where documentation is valued and emphasized.
7. Develop a schedule for future updates
Create a system for continuous assessment to ensure that the documentation is regularly reviewed and updated. Process errors can be found and fixed in a timely manner if reviews are conducted often. Additionally, it speeds up the process.
8. Assign accountability
One of the most important aspects of effective documentation is assigning responsibility.
All parties involved must understand their specific duties in the documentation process. Make it clear who’s responsible for enforcing documentation standards and keeping everyone accountable.
9. Keep up with frequent updates
The process of documenting anything is not something you can do once and leave alone. It’s an ongoing process that requires constant attention and revision.
Be careful to regularly review and update your documentation to keep it relevant. Instruct those with a stake in the documentation process to update it with any necessary changes, such as new policies, guidelines, or processes.
Start your IT documentation today
IT professionals and MSPs may provide more trustworthy service to their clients with the help of IT documentation.
Particularly, IT documentation samples and templates can help IT service providers know what information to add. Documentation updates can also go more smoothly with the help of these templates.
The documentation process might seem overwhelming, but it doesn't have to be.
Thanks to Scribe, hours of wasted time spent manually copying and pasting screenshots are a thing of the past. Scribe turns any digital process into a step-by-step guide—instantly.
Just turn on the extension and run through your process. Scribe will auto-generate a comprehensive document detailing your procedure in only a few seconds. You can incorporate the how-to manuals created by Scribe into your company's internal help center, wikis, knowledge bases, etc. It's the strongest way to align and train your IT team.












